•What hackers really do into our device?
•They can take all from our device and then disappear.
•Spyware (malicious software that enters a user’s computer, gathers data from the device and user, and sends it to third parties without their consent), odd advertisements and even a bank account or stolen identity.
•Cyber-criminals(people who use the internet to commit illegal activities. They hack into computers, steal personal information, or spread harmful software) may access routers, phones, computers, and even the most innocent camera.
New programs installed
•On the computer, we may see additional programs or files in some cases. It may have been hacked if new programs were installed on the computer.
•New programmes or files were added to the operating system or another piece of software.
•For case, a check box validating the installation of new toolbar or antivirus software is common in plugins and other free products.
•Further new programmes will be installed if you do not uncheck these boxes.
How do I know if my computer was hacked?
•On a computer, the most typical programs installed after it has been hacked are trojans and backdoors.
•These programmes can give a hacker access to a lot of information on our computer.
•Another typical approach for a hacker to gain access to a computer or remotely manage thousands of computers is using IRC clients(Software in the user’s computer that allows connection to IRC (Internet Relay Chat) servers on the Internet).
•Again Computer may have been hacked if we never participated in an IRC chat and have an IRC client.
•Our computer may be infected through a download or by visiting a hijacked website while you are surfing the Internet.
Computer passwords have changed
Online passwords
•After getting access to an online account, the hacker may change the passwords of one or more accounts.
•Try to reset the password with the assistance of the lost password option.
•Please contact the service provider if the forgot password option is not working or if your e-mail address has changed.
•They are the only ones who have the ability to reset our account and regain control.

Local computer password
•It can be possible that our computer’s password has been changed.
•It’s impossible for a password to change on its own.
E-mail sending spam
•When attackers hack our email address, they use it to distribute spam and malware to others.
•If we are sending commercial e-mail to our friends, family, or co-workers, our e-mail account may have been hijacked.
•Logging into our e-mail account will allow us to change our account password.

Increased network activity
•An attacker must connect remotely in order to gain control of a computer.
•If someone is remotely connecting to our computer, our Internet connection will be slower than before.
•Furthermore, after being hacked, a computer usually converts into a zombie that assaults other computers.
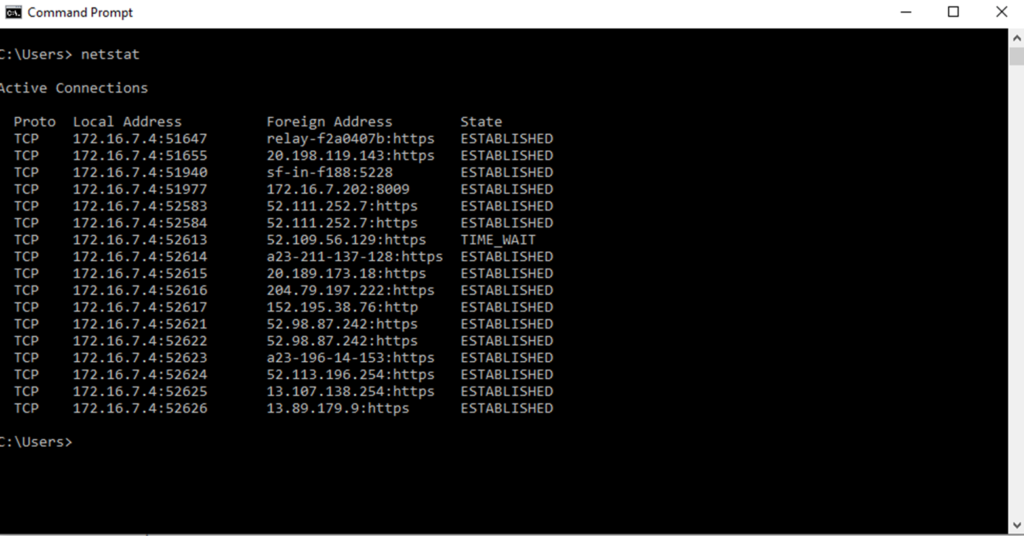
•We may check which programmes are using our computer’s bandwidth with the help of installing a bandwidth monitor computer application.
•The netstat command can also be used by Windows users in order to check for external network connections and open ports.
Videos suddenly buffer and web pages takes time to load
•Buffering occurs during a streaming video unexpectedly.
•Particularly, if not our Wi-Fi connection is poor or if we watch a lot of movies, this is a common inconvenience.
•On the other hand, Internet traffic can be slow down when malware hijacks DNS.
•This will slow our internet connection.
•For instance, when we enter our online bank’s website, if our router’s DNS settings have been hijacked, we will be directed to a phishing website.
•Online tools like F-Secure Router can also be used in order to check your router’s DNS settings.
•A safe router and home Wi‑Fi help us stay protected against online criminals and DNS hijacking. F‑Secure Security Cloud is a cloud-based system for cyber threat analysis that is operated by F‑Secure.
•Consider switching to a DNS server that offers strong hijacking prevention, such as Cloud Flare or Quad9.


Frequent, random popups
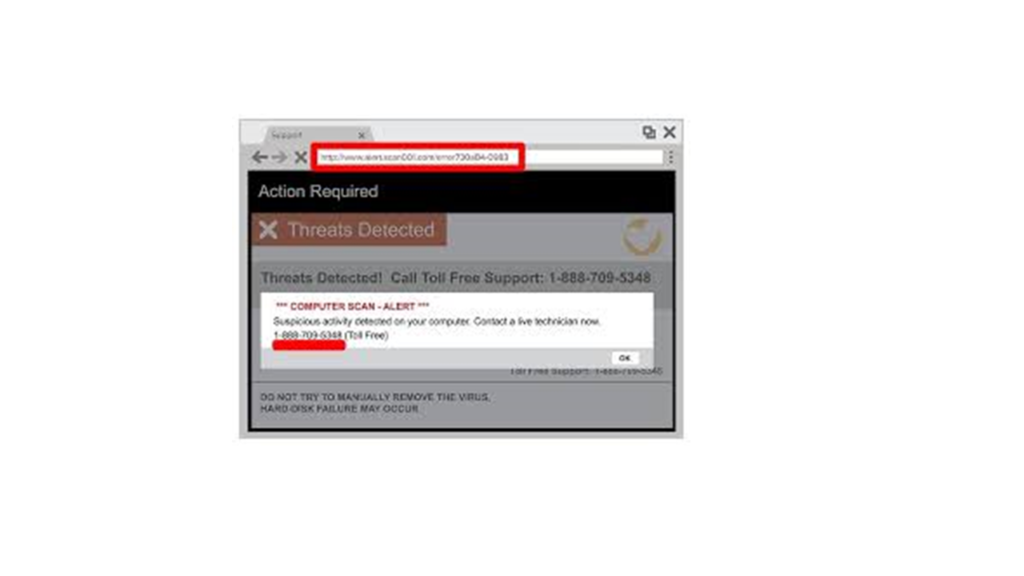
•This is a common symptom and it is the most irritating.
•If we notice random browser pop-ups from websites that don’t normally produce them, our system has been hacked.
•It’s like a spam email but much worse.
Unwanted browser toolbars
•This is a common exploitation sign-in which multiple new toolbars have appeared in our browser, each with a name that suggests the toolbar is intended to assist us.
•It’s time to get rid of the fake toolbar unless we recognize it as coming from a well-known vendor.

Unknown program requesting access
•Firewalls and computer security software help limit access for security reasons.
•It’s possible that wrong programmes have been installed or that our computer has been hijacked if it requests access to apps you don’t recognise.
•We recommend restricting access to an application if we are not sure.
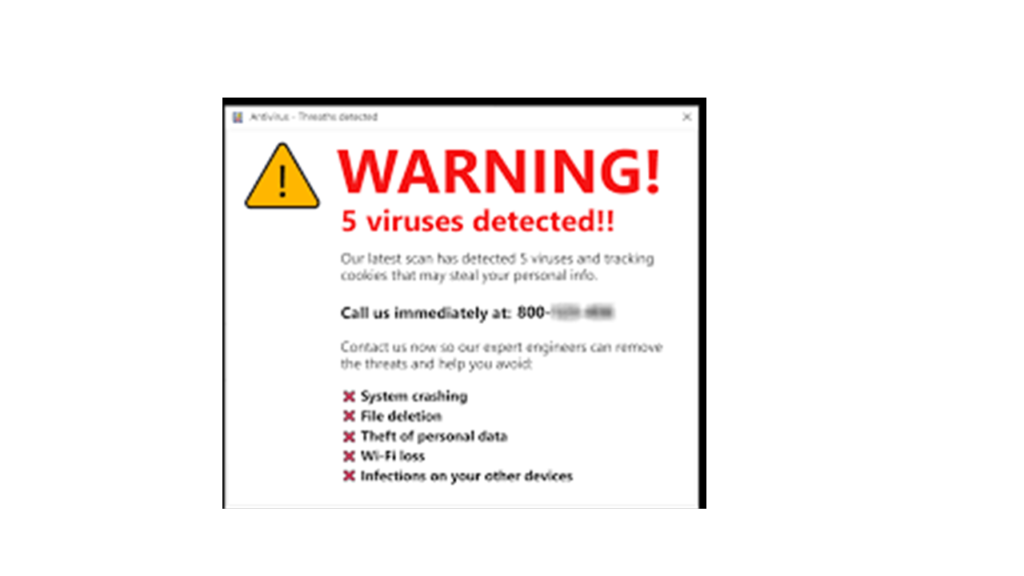
A fake antivirus message
•Our computer or mobile device displays a pop-up notification informing us that it is infected.
•The pop-up message poses as an antivirus scanner, claiming to have found a dozen or more malware infections on your machine.
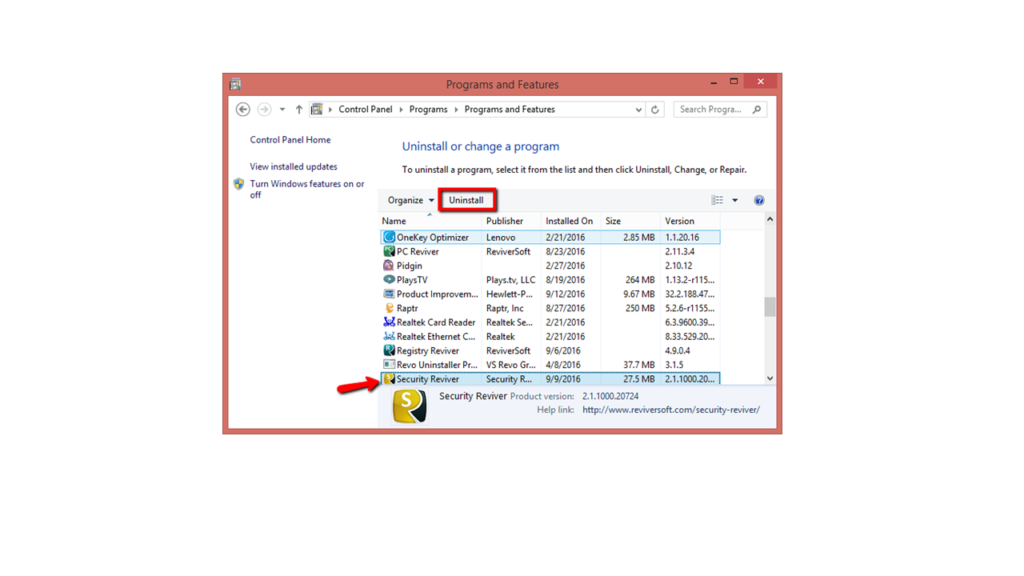
Security program uninstalled
•It is also a sign of a compromised computer if the antivirus, anti-malware, or firewall programmes have been uninstalled or disabled.
•These programmes may be disabled by a hacker in order to hide any alerts that may appear while you are using the computer.
Computer is doing things by itself
•A criminal third party might take control of our computer remotely if it has been thoroughly compromised and execute any programmes we have given permission to run.
•They can even control the computer as if they were sitting at our desk, using our keyboard and mouse, assuming they are in control of your current login session.
•A mouse pointer, for example, might be moved or text entered.
Internet browser homepage changed or new toolbar
•If our web browser settings have abruptly changed, it might be an indication of a virus or malware infestation on our computer.
•Unexpected browser changes include our default search engine switching to something we do not want, our homepage switching, and the installation of a third-party toolbar.

Online password is not working
•When your online password is not working, it may be a sign that it is hacked.
•For example, we are entering our online password correctly, but we are not able to access our account, or the password is not working.
•Sometimes, sites experiencing technical difficulties do not accept the correct password for a short time.
•It may possible that the hacker logged in to our account with the help of using our password and modified it to keep us out.
•And the hackers utilize it to gather someone’s secret information, changes the password.
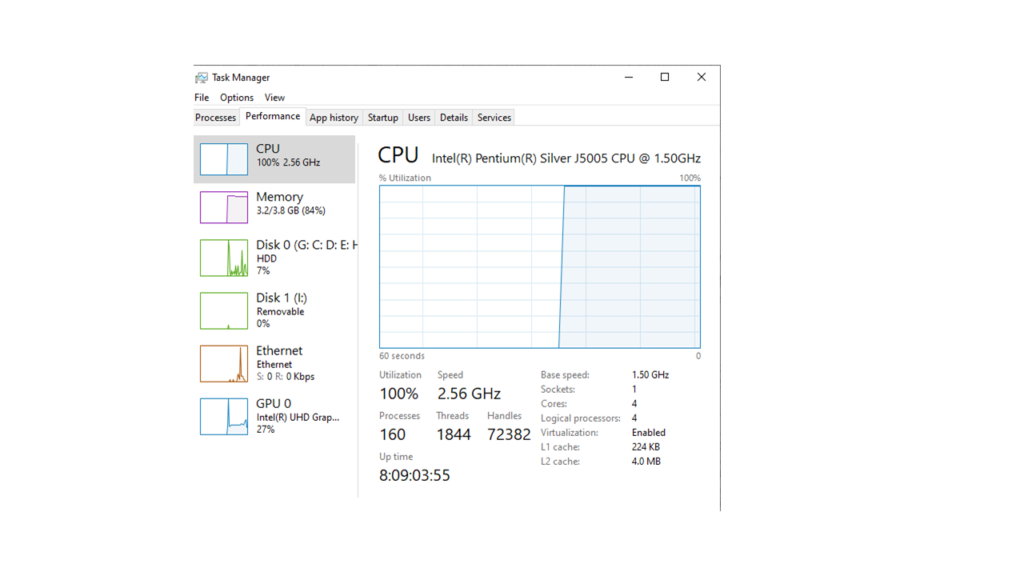
Computer Performance Decline
•An abrupt drop in performance is one of the most visible effects of hacking.
•We will have less accessible resources as hackers utilize system resources such as CPU, memory, and bandwidth.
•Starting up might take a long time.
•There may be a lot of network activity going on at the same time.
Unknown Social Media Requests
•If we get random access alerts on social network accounts, it is possible that our devices has been hacked.
•Non-technical approaches are increasing by hackers in order to steal personal info.
•They pretend to be buddies on the internet.
•They may phone us and claim to be from our Internet provider in order to obtain our system credentials and personally identifiable information (PII).

Prevention is the best cure